|
Innovative software package downloads from the featured in download webs sites! Investigate the featured software programs classes, watch the hottest renews of the cutting-edge apps, and acquire now! Do not toss away an option to acquire the best software: apply SoftEmpire directory to test applications for free. Have a look on the collection of free utilities and software app trials. Search among system utilities, acquire manipulators, softwares for fun, and all other varieties of software for your PC or mobile stuff!
Internet utilities and tools for home and business. Programs for file sharing, download managers and e-mail software. Free download.
|
Document Trace Remover
|
|
Download
|
Buy now!
|
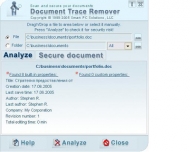
View screenshots
|
Vendor Price: $ 39.95
License: Shareware
File Size: 1.45 Mb
Version: 3.3
Release Date:
19 Feb 2008
OS: Win95, Win98, WinME, WinNT 3.x, WinNT 4.x, WinXP, Windows2000, Windows2003, Windows Vista Starter, Windows Vista Home Basic, Windows Vista Home Premium, Windows Vista Business, Windows Vista Enterprise, Windows Vista Ultimate, Windows Vista Home Basic x64, Windows Vista
System Requirements:
Windows 95/98/ME/NT/2000/XP/2003/Vista
Company: Smart PC Solutions, Inc.
|
|
A leaked document can compromise trade secrets and threaten company security. But did you know that even a document that you send or publish may also contain sensitive information that may harm your privacy and company security? Every time you create a document in a Microsoft Office application such as Word or Excel, it is automatically and compulsory tagged with extra information. All documents are assigned properties that list the document's author, organization name, document change and reviewing history, any comments made by the different editors, editing time, and so on. This information can be useful when working with documents in a workgroup, but may cause unwanted problems should it become available to a third party, putting your company in an embarrassing situation or even causing financial risk. A line or a paragraph of text that contains sensitive information, even if it is cut, deleted or overtyped, may still be stored in the document's metadata under certain circumstances, such as if text change tracking is enabled. Do you want all the notes made by your workgroup members while editing a presentation made publicly available? Document Trace Remover checks your company workflow, including Microsoft Word documents and Excel spreadsheets for unwanted private information that may infringe your privacy and threaten company security.
Document Trace Remover discovers all types of meta-information and offers you an easy way to remove any hidden data from your documents. When this is done the documents no longer contain a single trace of infringing information. Batch mode is available to quickly clean multiple documents. Make Document Trace Remover part of your routine workflow! Run Document Trace Remover every time before publishing or sending the document out of your company to ensure highest level of privacy and security of your workflow.
|
More to download:
Spyware Interrogator - Tech Edition
SSI Tech Edition is the ultimate free malware research utility. Clean up HijackThis logs using spywaredata.com's online database, ADS discovery, and internet traffic watch!
Clean Space
Clear computer tracks and garbage: delete browsing history, cookies, temp files, cache, logs, recent searches, autocomplete history and other tracks. Clear your computer from evidences of your activity.
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Sexy wallpaper changer & screensaver. New pics auto-downloaded every day!
Sexy 3D digital babes dance and strip naked in full screen virtual reality...
The Ultimate Goldfish Aquarium, featuring amazing and unique Goldfish
|
|

