|
Free software package acquisitions from the greatest in download websites! Investigate the asked-for software system groups, ascertain the most recent releases of the notable programs solutions, and get at once! Do not fail opportunity to try the first class apps: apply SoftEmpire directory to test software program for free of charge. Meet the collection of free utilities and package demo versions. Search among Windows programs, download manipulators, softwares for relax, and all other varieties of software for your notebook or mobile phones!
List of utility software downloads for free and relief prices!
System software for development, administration, and support of your computer best practices.
first-class Disk utility software downloads for Windows 7.
Utility software for Mac reviews champions! Get the maximal from your Mac with SoftEmpire!
|
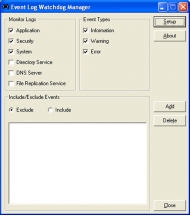
Event Log Watchdog
|
|
Download
|
Buy now!
|
View screenshots
|
Vendor Price: $ 35
License: Shareware
File Size: 89.67 Mb
Version: 3.0
Release Date:
20 Sep 2007
OS: WinXP, WinNT 4.x, Windows2000, Windows2003
System Requirements:
Windows 2000, Windows XP, Windows 2003, .NET Framework
Company: Keroon Software Corporation
|
|
Event Log Watchdog monitor's your Windows Event Logs and notifies you via Email or Syslog when a new event is logged. You can define which Event Logs you wish to monitor and what types of events you wish to receive Email notification of. One license per machine.
|
More to download:
Watchdog - O - Matic
Watchdog - O - Matic is a software watchdog that monitors and diagnoses any program you want. Watchdog - O - Matic will automatically solve any problems the monitored application encounters and it will restart the program if it crashes or hangs.
Duke: The Portfolio Watchdog
Duke, the Portfolio Watchdog, tracks and monitors your stock movements, updates prices every 30 seconds, and makes recommendations about when to buy and sell your stocks (see screenshot). Duke will also track your gains and losses and current quo...
OAK WatchDog
A small utility for monitoring computers in the local network which place itself in the tray and tells you about remote computers state. Up to 4 remote computers can be monitored. Different kinds of actions can be done on remote computer state ch...
Prevent Deletion
Prevent the deletion of certain files/folders on a shared drive in your network. This program will check whether a specific file exists on a shared drive, and if not, recopies the file. This process is repeated at a defined interval of time.
Event Alarm
Event Alarm is a powerful and cost-effective way to keep tabs on the health and security of your network. Event Alarm offers the network administrator a wide range of notification options including email alerts, network popups, pager calls, or br...
Event Manager (10 user license)
This page is for purchasing a 10 user license for Event Manager via our online store run by Regnow.com | Digital River. After placing your order, you will receive an emailed receipt from Regnow.com. Program download information, an unlocking code...
DLL Show 2000
DLL Show is a small utility that displays a list of all running processes and their DLL dependencies. Click your mouse on a listed task or process to see the DLLs that process uses. DLL Show displays comprehensive information about running processes.
SkimStart
SkimStart is a powerful Windows utility program that helps you to have one-click access to all your favourite files. It helps you to organize your notes and quick start hidden windows utilities.
Collectorz.com Euro Converter
Small but useful utility that allows for quick conversion from Euros to the "old" currencies of Euro-countries, and vice versa. Features: sits in system tray, Always On Top...
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Thumbzilla allows you to create thumbnails from images (JPG and GIF) and mov...
DHTML Menu Builder which enable you to create perfect web menus of all kinds
Free Calendar Webpart to substitute for standard Webpart for SharePoint 2003...
|
|

