|
Be prepared for the greatest software application download practice you have ever felt! Open the numerous software program sub categories, check the fresh updates of the widely known tools, and download software programs for free. Take special admission to all sorts of laptop apps: business tools and utilities, games, security solutions, and many others. The Softempire ultimate software catalog becomes larger permanently! Every new hour brings excellent new software applications here, the best software tool downloads. Try now and recieve a result!
Computer utility software downloads. The greatest programs for Windows, Linux, and Mac!
System software projected to help explore, configure, optimise, and maintain the computer.
Hard drives utility diagnostic tools to test the physical media.
Windows utility software tool collection to value, organize, and perfect the activities of the computer.
|
Keylogger
|
|
Download
|
Buy now!
|
View screenshots
|
Vendor Price: $ 15
License: Shareware
File Size: 0.71 Mb
Version: 0.9
Release Date:
5 Mar 2008
OS: Win98, WinME, WinNT 3.x, WinNT 4.x, WinXP, Windows2000, Windows2003, Windows Media Center Edition 2005, Windows Vista Starter, Windows Vista Home Basic, Windows Vista Home Premium, Windows Vista Business, Windows Vista Enterprise
System Requirements:
none
Company: Keyservice
|
|
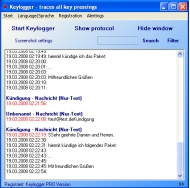
Keylogger protocols all Keystrokes with screenshots also if they input in other programs or windows. Keylogger shows this "click protocol" clearly together with date and time of input and headline of the used window.
All click protocols will be stored with a strong encryption (with AES - Advanced Encryption Standard). Keylogger can work invisible in a "Stealth mode". It means, then program window will only be remain visible if the correct password is put into (any other window). In the "task manager" the program has the name "ccmd.exe" - also you can change the name with a simple menu function. Also there is a menu function to completely remove the software from the computer.
Keylogger available for free download and free testing without restrictions. Only the "stealth mode" works only for maximum 15 minutes. After than keylogger remains visible. THe registration code can be ordered by PayPal - in some seconds, if you want. To end of april in 2008 registration costs only 9, 95 ?.
|
More to download:
Printfil - Windows Printing System
Allows character based apps (DOS-Windows-Unix-Linux) to print to ANY Windows printer, including USB, network printers, faxmodems and PDF writers. It can also capture LPT out and redirect the jobs, even if a printer is phisically connected to the port
Image To PDF
Image To PDF can directly convert dozens of image formats, such as TIF, JPG, GIF, PNG, BMP, PSD, WMF, EMF, PDF, PCX, PIC and so on, into PDF format.
Image To PDF COM/SDK Unlimited License
Image To PDF can directly convert dozens of image formats, such as TIF, JPG, GIF, PNG, BMP, PSD, WMF, EMF, PDF, PCX, PIC and so on, into PDF format.
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Sexy wallpaper changer & screensaver. New pics auto-downloaded every day!
Sexy 3D digital babes dance and strip naked in full screen virtual reality...
The Ultimate Goldfish Aquarium, featuring amazing and unique Goldfish
|
|

