| Editor's choice |
Free Lepide DC Monitor
Lepide DC Monitor tool to analyze status of active directory domain controllers
Reboot Buddy
<a href="http://www.vsisystems.com/rebootbuddy.htm">Auto
Computer Security
Keep your computer's content protected! Hide or shred files, lock applications.
SIM Card Recovery Tool
SIM card SMS reader utility restores lost or deleted contacts and text messages
WISeForm
Access Web sites with one password, trusted digital identity, fill forms easily.
Disk Wiping Software
Disk wiper utility wipes selected or whole data from USB drive and hard disk
Convert OST to PST
Convert OST to PST tool to convert unusable Exchange OST file to PST file.
|
|
Excellent software tool gettings from the best in download catalogs! Surf the asked-for package lists, check the latest renews of the amazing programs apps, and setup now! Do not miss an advantage to test the greatest solutions: employ SoftEmpire website to try computer software for free. See the aggregation of freeware and computer software trials. Choose among Windows and Linux programs, acquire planners, playgames, and all other forms of software apps for your laptop or cell accessory!
|
|
|
|
Download
|
Buy now!
|
|
Company: JCMatt software
OS: Win95, Win98, WinME, WinNT 4.x, Windows2000, WinXP, Windows Vista Starter, Windows Vista Home Basic, Windows Vista Home Premium, Windows Vista Business, Windows Vista Enterprise, Windows Vista Ultimate
Description: Small, easy to setup, security program that locks your computer while leaving the display visible. Once locked your system can not be accessed until the unlock password is entered.
Screenshots:
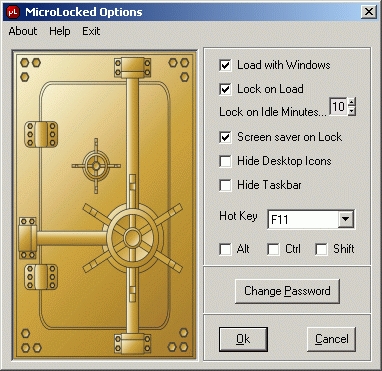
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Sexy wallpaper changer & screensaver. New pics auto-downloaded every day!
Sexy 3D digital babes dance and strip naked in full screen virtual reality...
The Ultimate Goldfish Aquarium, featuring amazing and unique Goldfish
|
|

