| Editor's choice |
DDD Pool
Highly addictive pool simulation with cutting edge 3D graphics & smooth
FreeGamia Projectgnh20
A large and mysterious world that lives not around the main character, but..
Super Solitaire Deluxe
Super Solitaire Deluxe includes about 450 solitaire card games .
FreeGamia Zomback
A terrible virus has turned most of the innocent rural peasants into bloodthirst
Wall Street Raider
Wall Street stock market/corporate financial simulation and learning experience
Freecell 2003
Freecell 2003 is the highest rated Freecell on the web. It has a lot of cool...
Star Defender
High-quality arcade with excellent graphics and breathtaking gameplay.
|
|
Get tool swiftly and without troubles. Our library is happy to demonstrate a big assortment of the splendid free software, shareware, and software systems. On this directory you be able to acquire demo releases of popular paid programs, and recieve the greatest free software for your PC or mobile appliance,gadget. Search an ultimate group of the best new software programs on our library! Test trial editions and setup advanced apps on the computer or cellular appliance. Have a look on the recent versions and new releases of typical applications, last software solutions, and PC utilities! Try today!
A large source of great free games including arcade games, strategy games, sports games, puzzle games and more.
|
|
|
|
Download
|
Buy now!
|
|
Company: MetalShard, inc.
OS: Win98, WinME, WinXP, Windows2000, Windows CE
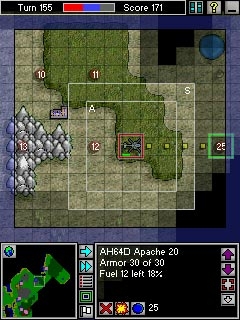
Description: Pocket War is a strategic turn-based war game much like the old Empire or Galacitc Conquest games. By choosing what to manufacture and sending orders to your troops, you give your troops the guidance they need to vanquish the computer.
Screenshots:
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Thumbzilla allows you to create thumbnails from images (JPG and GIF) and mov...
DHTML Menu Builder which enable you to create perfect web menus of all kinds
Free Calendar Webpart to substitute for standard Webpart for SharePoint 2003...
|
|

