| Editor's choice |
Kingston Memory Card Recovery Tool
Kingston memory card recovery utility rescue pictures from formatted memory card
paEggBasket
Security codes and passwords really shouldn't be carried around on your hand...
Backup4all
Customizable backup program. Full, incremental, differential and mirror backups
Professional Data Recovery...
Professional Data Recovery tool previews files before actual retrieval from HDD
Spices.Fortress
Easy-to-use, affordable and elegant C# 2.0 trial and demo version creation tool!
Cipherlok
Easy to use Blowfish based file encryption using passwords or USB Tokens
Free Keylogger r
Reliable Free Key logger application system tracks file folder access informatio
|
|
Download utilities for disk management, hard disk utilities, software for disk recovery, disk scan, disk wipe, disk management freeware, disk tools for windows.
|
Recover Lost File Software
|
|
Download
|
Buy now!
|
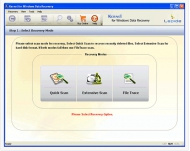
View screenshots
|
Vendor Price: $ 49
License: Shareware
File Size: 3.15 Mb
Version: 14.0
Release Date:
2 Dec 2014
OS: Win2000, Win7 x32, Win7 x64, Win98, WinServer, WinVista, WinVista x64, WinXP, Win8, Win8.1
System Requirements:
Pentium II 400 MHz, 64 MB RAM, 10 MB
Company: Recover Lost File
|
|
|
More to download:
Directory Snoop
File search, recovery, and wipe utility for Windows. Recover deleted files and data from individual clusters. Display raw directory structures and purge erased file names. Snoop through files and clusters with advanced search functions.
Clipstory
We all use Copy and Paste all the time, but the problem is that you can only copy and paste one thing at a time. What's needed is a way to copy and paste to the clipboard, and see the history; and that's why we call our new application Clipstory!
Convert OST into PST File Format
How to convert OST into PST file format quickly and easily? Use OST to PST Converter. This user-friendly tool allows to preview the offline mailbox content and to save the data in PST, MSG, DBX, and EML formats in any location.
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Sexy wallpaper changer & screensaver. New pics auto-downloaded every day!
Sexy 3D digital babes dance and strip naked in full screen virtual reality...
The Ultimate Goldfish Aquarium, featuring amazing and unique Goldfish
|
|

