|
Recieve software tool swiftly and handy. Our catalogue is cheerful to demonstrate a handy diversity of the excellent free software, shareware, and software solutions. On this catalog you be able to try trial releases of popular marketable programs, and setup the top free software for your laptop or mobile appliance,gadget. Discover an excellent library of special fresh solutions on SoftEmpire! Test demo editions and get recent apps on the PC or digital phone. See the recent versions and new releases of general applications, last programs, and PC tools! Get for free!
Free utility software downloads for Windows, Mac, and Linux. Top programs!
System software to advance your computer performance. Make the PC quicker, and the in high degree secure!
Hard drives utility diagnostic tools to try out the physical media.
Windows XP utility software free downloads to deal files, registry, rights, and the entire system!
|
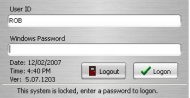
The Lock
|
|
Download
|
Buy now!
|
View screenshots
|
Vendor Price: $ 45
License: Shareware
File Size: 22.06 Mb
Version: 5.08.0505
Release Date:
5 May 2008
OS: Win98, WinME, WinNT 4.x, Windows2000, WinXP, Windows2003, Windows Vista Home Basic, Windows Vista Home Premium, Windows Vista Business, Windows Vista Enterprise, Windows Vista Ultimate
System Requirements:
256MB Ram required, 512MB or more on Windows 2000 or later recommended
Company: CrashCourse Software
|
|
The Lock provides user audit, access control, Internet and system security for any computer running Windows 2000, Windows XP (with or without Fast User Switching), Windows Server 2003, and now supports Windows Vista. Running on Windows 9x/ME will work, but is no longer supported.
The Lock is PL-1 compliant to Chapter 8, NISPOM. It also meets Sarbanes-Oxley Access Control, Intrusion Detection, and PC Auditing requirements, as well as meets HIPPA, Access, Authorization, and Security control requirements.
All user security is group based configurable by any members of the Administrators group. User security can define system policy, logon times, internet access times, web site restrictions, and access to local resources such as programs and files and folders, including removable media (USB, flash, etc.), that can be restricted as it is plugged into the system. Restrict printer access in any Windows application. Restrict access to screen capture via the Print Screen key. Logging features will record web sites visited, programs run, and any security violations occurring while the user is logged in, and now supports the Firefox browser.
User security data is stored locally or on a shared network folder.
The Lock the local Windows system, a Netware Server, a Windows NT server, or a remote Lock Security Manager server, can verify user passwords.
The Lock has a built in cloning feature designed to make network installations a simple one step process. When used in conjunction with the Lock Security Manager Server, all remote systems may be kept up to date when The Lock has been updated on the SMS system. Tools are included with the Security Manager that will allow remote monitoring of any systems running The Lock and connecting to the Security Manager.
Active Password monitoring is used to combat modification of Windows 2000/XP/2003 user passwords (usually with a bootable hacking disk) outside of the Windows GUI.
Interface is now skinnable.
|
More to download:
FileSpy
FileSpy allows users connected to a network with Novell Netware to see all the users who are using a specific file. It also allows viewing of the user's rights to the file/directory, how the file was opened, the user's network address, and the da...
AdRem NetCrunch
NetCrunch 5 offers agentless policy-based monitoring of Windows, Linux, NetWare and SNMP devices in one package. It centralizes fault management, collecting, alerting and delivering performance reports on events from SNMP sources, Windows Event Logs.
AdRem Server Manager
OES/NetWare/Linux server performance monitoring and reporting (CPU, memory, NLMs, network performance); user/connection monitoring (e.g. opened files, requests); file/directory/volume/trustee management; multi-server configuration.
DISLIN for MS Visual C++
DISLIN is a high-level and easy to use plotting library for displaying data as curves, bar graphs, pie charts, 3D-colour plots, surfaces, contours and maps. Several output formats are supported such as X11, VGA, PostScript, PDF, CGM, PNG and TIFF.
Z-Desk
Running as a menu- and borderless fullscreen program, Z-DESK consists of a number of screens designed after the computer displays in Star Trek:The Next Generation and Star Trek:Voyager. It enables you to start programs and desktop items, set up '...
PASSPORT PC TO HOST
PASSPORT PC TO HOST provides Windows-based TN3270, TN5250, SCO ANSI, VT100 and VT220 telnet terminal emulation for Microsoft Windows Includes Visual Basic and VBscript support, can be deployed using SMS, MSI, Citrix or Microsoft Terminal Server.
Password Keeper 2000
Password Keeper is a small utility useful for storing your frequently used passwords. Password information can be stored, edited and printed with this easy to use program. Each password file that you create can contain up to 1000 account entries.
PPT2EXE Packer
Encrypt your ppt document,support ppt,pptx,pps,ppsx;Protect the distribution of your ppt document,No editing,No copying,No printing,stronger than the MS office's own encryption;PPT2EXE,pps2exe,pptx2exe,ppsx2exe
Free Comodo AntiVirus
If you?ve installed our Firewall, you?ve built up a solid wall of defense for your PC. But what about malware that?s found its way inside, or a tricky viral program you?ve allowed to execute? Comodo AntiVirus is your weapon against PC invaders.
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Sexy wallpaper changer & screensaver. New pics auto-downloaded every day!
Sexy 3D digital babes dance and strip naked in full screen virtual reality...
The Ultimate Goldfish Aquarium, featuring amazing and unique Goldfish
|
|

