|
Excellent software program gettings from the most popular in download sites! Surf the popular software applications categories, learn the freshest versions of the amazing computers programs, and obtain now! Do not fail a luck to obtain the first class software programs: apply SoftEmpire directory to setup software solutions for free. Meet the aggregation of free programs and software package demo versions. Search among computer tools, acquire manipulators, softwares for relax, and all other sorts of tools for your notebook or mobile accessory!
Best computer utility software free downloads! take full versions and demos now!
System software for development, management, and support of your computer greatest patterns.
Top Disk utility software downloads for Windows 7.
Utility software for Mac reviews champions! Get the maximum from your Mac with SoftEmpire!
|
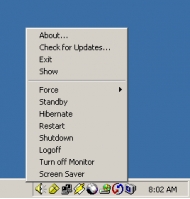
ShutdownTray
|
|
Download
|
View screenshots
|
License: Freeware
File Size: 0.18 Mb
Version: 1.3.2
Release Date:
24 May 2004
OS: Win95, Win98, WinME, WinNT 4.x, WinXP, Windows2000
System Requirements:
Visual Basic 6.0 Runtimes
Company: VicTech Software
|
|
ShutdownTray 1.3.2 allows quick and easy access to all of your system's power options (shutdown, restart, standby, log off, and more). It allows you quick access to shudown, restart, standby, hibernate, log off, turn off monitor and trigger the screen saver-you can also force a shutdown and a restart. Version 1.3.2 fixes an issue with confirmation for restart being asked in some cases when confirmation was turned off.
ShutdownTray is freeware, and requires the Visual Basic 6.0 runtimes (MSVBVM60.DLL) and the Microsoft Windows Installer (Preinstalled with Windows 2000, Me, and XP, instructions at http://www.victechsoftware.com/shutdowntray.html) to install.
|
More to download:
Iconic Tray
This tiny utility lets you minimize any window either to the system tray, or to a special new tray (see image). This helps you keep your taskbar clean for often used apps. Minimizing can be carried out with mouse clicks and/or system-wide hotkeys.
Passage: Path of Betrayal
Passage places you in a vast, fleshed out fantasy world of interwoven lands. Taking on the role of Riff, you'll travel throughout your world of Arkane as you delve deeper into the plot of danger and betrayal that has been set before you following...
AgentTray for 2000-XP
Optimization the Expanded list of last documents, wallpapper, the control of the autoloading, the built - in service of an exchange of messages.
ShutDownOne
Auto Restart or ShutDown. Auto Login, Privacy Control: IE history, cookies, typed URLs and more. Scheduled operation, Remote ShutDown, Batch shutdown, Password Protection, Hot Key, Silent Mode...
Auto ShutDown
Shuts your PC down at a pre-determined time. There are two main functions of ASD, firstly to reduce electricity consumption secondly to allow the user to leave the PC to finish a task, and not have to return just to switch the PC off. ASD support...
Smart Bomb PC Shutdown
A power-off utility with intelligence. Aside from being able to turn off your machine after a period of time, it can monitor CPU usage and Internet in order to delay shutdown while any processes in that regard are going on. Smart Bomb will allow ...
QVert
QVert is a quick and easy to use unit converter tool for Windows based operating systems. QVert supports most common and many not so common units of measure. Conversion units are separated into 15 different and unique categories...
7art Zodiac ScreenSaver
7art Zodiac screensaver brings you 12 amazing signs of the zodiac
pictured in original way. The 7art Zodiac screensaver will broadcast the magic of Astrology from
the Central Processing Unit of your PC.
Mountain Lake 3D Screensaver
Bathe in the warm sun rays as you travel around this beautiful mountain lake. Enjoy the view of the lush greenery on the banks contrasting with the quiet chill of the crystal water. The reflections on its surface have a truly mesmerizing effect.
|
|
|
Windows Backup |
Looking for backup software? Try Handy Backup - automatic data backup to DVD, CD, FTP, network, or Online. Client-server enterprise backup software.
|
|
Top Downloads |
Sexy wallpaper changer & screensaver. New pics auto-downloaded every day!
Sexy 3D digital babes dance and strip naked in full screen virtual reality...
The Ultimate Goldfish Aquarium, featuring amazing and unique Goldfish
|
|

